Russia blocks Tor: what has it achieved and what should the user do? | Russia and Russians: A View from Europe | Dw
The Tor browser is still working in Russia, although from the beginning of December 2021 the Russian authorities began to block its work. The number of users who directly access the Internet using the Tor anonymizer has decreased, judging by the Tor Project, a non-profit organization, but at the same time the number of those who bypass blocking using so-called “bridges” has increased dramatically (see infographic).
The Russian regulator Roskomnadzor (RKN) will add the main site of the anonymizer project, www.torproject.org, to the register of sites with “prohibited information” back in December 2017, but the project began to be blocked only a year later, officially from December 7, 2021, after of the project, according to RKN, “prohibited information” was discovered. True, the claims of the Russian regulator against Tor remain a mystery: following the link to the “forbidden information”, the user received data about the Tor browser itself by downloading it.
Nevertheless, now the authorities of the Russian Federation are blocking both the main site of the project and the mirrors, that is, copies of the main site at other addresses, and they also restricted access to the servers, using the Tor browser to communicate. “These IP addresses are publicly known, and they are also completely blocked,” said DW Stanislav Shakirov, technical director of Roskomsvoboda, which advocates for the protection of digital rights in Russia.
RKN, according to Shakirov, also made an attempt to block the very traffic that goes through Tor. For this Russian government they use a new DPI technology (deep packet inspection) – in Russia it calls TSPU (“Technical means of countering threats”).
Tor browser works in Russia thanks to “bridges”
The guarantee of Internet accessibility in Tor is the presence of the so-called “bridges” (in English bridges) inside the anonymizer. “The idea is that” bridges “are” a proxy server, there is an intermediary that gives access to the Tor network, “explained Stanislav Shakirov.
Some of the “bridges” are built into the Tor browser itself, and they have been blocked. But each user is able to independently create such “bridges” – how it works, the creators of the Tor project themselves explain in their own way. They communicate with the project via a message to the Tor Telegram bot, or by email, or add a bridge manually.
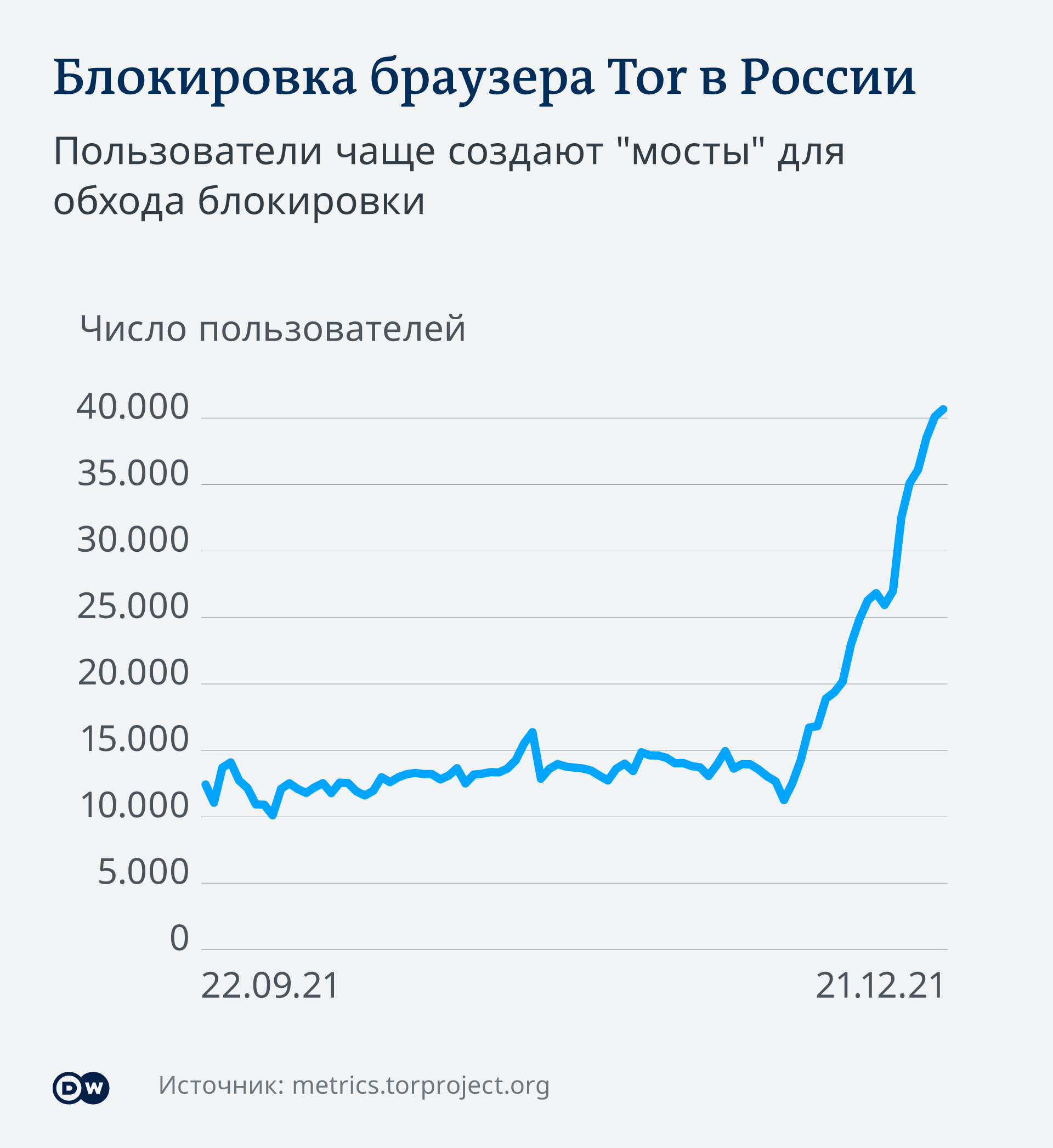
Oliver Linov (Oliver Linov), DW’s cybersecurity expert, is betting that users will create bridges on their own and thus keep free access to the network. “Bridges can be used to bypass government censorship. Even if Tor, as in Russia, is blocked, using” bridges “access to the Internet in the browser is possible,” says Oliver Linov. The fact is that it is practically impossible, according to him, to block the “bridges” created by ordinary users, since “new IP addresses are constantly appearing, and if you try to control Internet traffic, you will not be able to destroy them.” DW is also partnered with the Tor project, and the protected page URL is through this browser.
Blocking Tor is easier than Telegram
The Tor blocking situation is reminiscent of the RKN’s attempts to block the Telegram messenger, which began in 2018. However, the Russian authorities are technically more prepared today, says Shakirov. “Internet traffic”, which allows you to display traffic going, for example, through the Tor browser, explains the technical director of Roskomsvoboda. However, the new tools are not perfect either, Shakirov explains, Tor traffic is disguised as other types of traffic, and attempts to block the anonymizer via DPI carry great risks, for example, for video telephony over the Internet, which are not directly related to Tor.
So far, Shakirov considers the actions of the Russian authorities to be more a test of his capabilities than a real attempt to block the anonymizer. “If there is serious pressure, then the tactics can be the same (as with Telegram. – Ed.): pick up a bunch of “bridges” and distribute them in real time. After that, it will be impossible to block Tor to determine the obfuscated (disguised. – Ed.) Tor traffic is also impossible, “Shakirov explains. All bridges cannot be blocked, so no country would be able to completely block Tor,” says Stanislav Shakirov.
The technical director of Roskomsvoboda sees the main goal of the Russian authorities not so much in blocking an unwanted anonymizer as in monopolizing control over information in Russia. The effectiveness of state blocking lies not in stopping a super-motivated energetic person from going somewhere, says Stanislav Shakirov. He is confident that the effectiveness of blocking should be assessed by the extent to which independent media will be able to retain their audience if they are blocked in the Russian Federation.
See also: